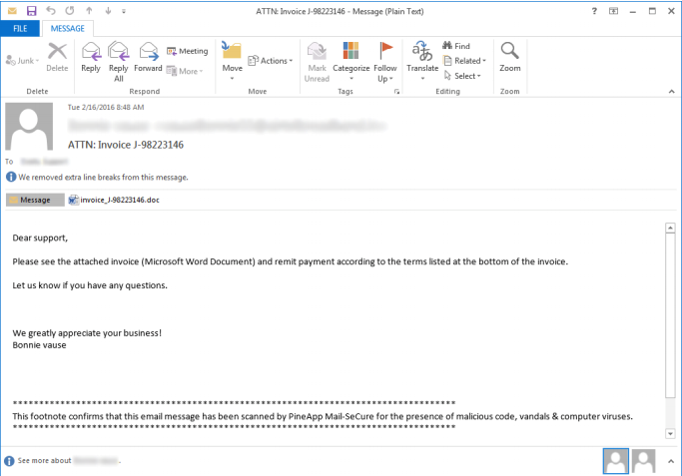
 A recent study of six million users shows the most common industries to fall victim to the inevitable phishing attack. Topping the list for highest percentage of "Phish-prone" employees in the small to mid-sized organization category was the insurance industry with a whopping 32.66% of employees failing the phishing test. In the lead for large organizations (1,000 or more employees) with the most "Phish-prone" employees, was the non-profit industry at 29.85%.
A recent study of six million users shows the most common industries to fall victim to the inevitable phishing attack. Topping the list for highest percentage of "Phish-prone" employees in the small to mid-sized organization category was the insurance industry with a whopping 32.66% of employees failing the phishing test. In the lead for large organizations (1,000 or more employees) with the most "Phish-prone" employees, was the non-profit industry at 29.85%.
The Phish-prone percentage is determined by the number of employees that would click on a simulated phishing email link or open an infected attachment as simulated by the conductor of the study, KnowBe4.
[RELATED: 3 Phishing Attack Examples]
The overall rankings for the most phish-prone industries are:
| Insurance | 32.66% |
| Manufacturing | 30.99% |
| Technology | 30.09% |
| Not for Profit | 29.85% |
| Retail/Wholesale | 28.14% |
| Energy/Utilities | 27.89% |
| Healthcare/Pharma | 27.75% |
| Other | 27.39% |
| Education | 27.16% |
| Business Services | 26.74% |
| Financial Services | 26.29% |
| Government | 25.09% |
Phishing attacks prove time and time again to be one of the most effective forms of cyber-attacks. To put it in perspective, legitimate B2C marketing emails average a click-through rate of 2.4%. Legitimate B2B marketing emails receive an average click-through rate of 3.5%. Illegitimate phishing emails average a click-through rate of 13%! Users are five times more likely to click on a phishing email than a marketing email.
Don't believe it? Pine Cove is happy to set up a phishing email simulation for your organization.
What's the Solution?
There are basically two steps every organization should take to protect themselves from the inevitable phishing attack. First, organizations need to train employees how to recognize phishing emails. Phishing emails can be hard to recognize but there are some best practices that users need to know when evaluating whether or not an email is legitimate.
Second, its safe to assume that no matter how much training you give, users will still fall victim to cyber-attacks and malicious emails. To secure your assets, organizations should invest in cyber-security software and hardware which will prevent the malicious infection from accessing your organization's assets.