 Cyber-criminals are aggressively targeting laptops, desktops, servers, and even mobile devices. From a single device to entire networks, they infect as many devices as they can to mine for cryptocurrency on. Simply put, you do the work, pay for the electricity and hardware, and they pocket the rewards.
Cyber-criminals are aggressively targeting laptops, desktops, servers, and even mobile devices. From a single device to entire networks, they infect as many devices as they can to mine for cryptocurrency on. Simply put, you do the work, pay for the electricity and hardware, and they pocket the rewards.
Cryptojacking and cryptomining are two terms that are used to describe the dangerous practice of cyber-criminals using your technology to mine cryptocurrency such as bitcoin, ethereum, and more. These cyber attacks that could be infecting your computer without you even knowing. So let's discuss how we can fight back against this practice but first, some background information. While the terms cryptojacking and cryptomining are sometimes used interchangeably, there are a few key differences.
Cryptomining is the act of doing all the necessary – and quite frankly very complex – effort required to generate and work with cryptocurrency. It can be both legitimate or malicious, which is determined by several factors, most significantly whether you consciously agree to it.
Cryptojacking is malicious cryptomining. The crooks get code onto your devices without your permission to mine for cryptocurrency using your equipment and your resources. They keep all the proceeds themselves while you get nothing for your hard work.
Cryptomining is a legitimate practice but some criminals have seized this opportunity to mine maliciously. The difference between legitimate mining and malicious mining really comes down to intent. Legitimate and malicious mining are the same in almost every sense except who gets paid and whether the person who owns the device performing the mining willingly chooses to participate.
Negative implications of cryptojacking
Cryptojacking might sound like a relatively harmless cyber-attack at first – it doesn’t need to read your personal data, or even to access to your file system. However, the downsides are still very significant:
1. Unbudgeted operating expenses from powering computers to work for someone else.
2. Opportunity costs because legitimate works gets slowed down. You think your computer is slow now, wait until you get cryptomining software on it!
3. Security risks from who-knows-what untrusted programs and network connections.
4. Reputational and regulatory costs of reporting, investigating and explaining the cryptomining activity.
5. Ethical concerns of allowing employees to mine using your resources.
Fight back against cryptojacking
When it comes to stopping cryptojacking there is no silver bullet. Just like protecting yourself against ransomware, you need to take a layered approach to protection.
1. Block websites hosting JavaScript miners both at the gateway and the endpoints
2. Stop cryptomining malware at every point in the attack chain
3. Prevent cryptomining apps from running on your network
- We also recommend that you:
• Keep your devices patched to minimize the risk of exploit-related attacks
• Use mobile management technology to ensure that native mobile apps aren’t present on your mobile phones or tablets
- Educate your team:
• Cryptomining is not an acceptable use of company resources or power
• Explain traditional attack vectors of malware such as phishing and how they can protect themselves
- Maintain a strong password policy
- Keep an eye out for the tell-tale signs that you’ve been cryptojacked:
• Slow network
• Soaring electricity bill
• Spike in CPU consumption
Cryptojacking is a sophisticated practice that can be hard to understand. If you want to learn more, we recommend downloading out this cryptojacking whitepaper.
How Sophos Security protects against cryptojacking
Sophos offers a range of technologies to protect you at every point in the attack chain.
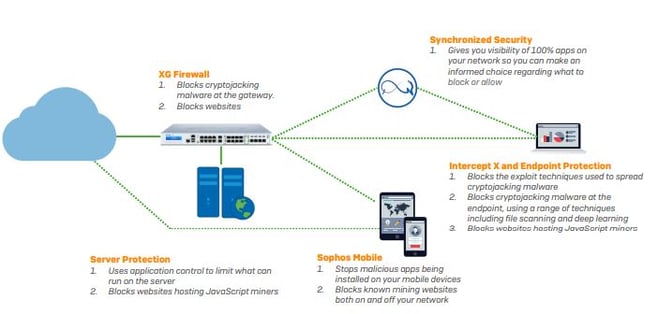
- Sophos Central gives you Intercept X, Endpoint, Server, and Mobile protection, all managed through a single, intuitive console.
- Sophos XG Firewall, our NSS Labs-recommended appliance. You can run it in-line with your current appliance and see the difference.
[RELATED: Why Sophos Security | Pine Cove's Top 5 Reasons] [Read more Cyber-Security Blogs]
Sign up for a free IT assessment to see if your cyber-security can protect you against cryptojacking.













