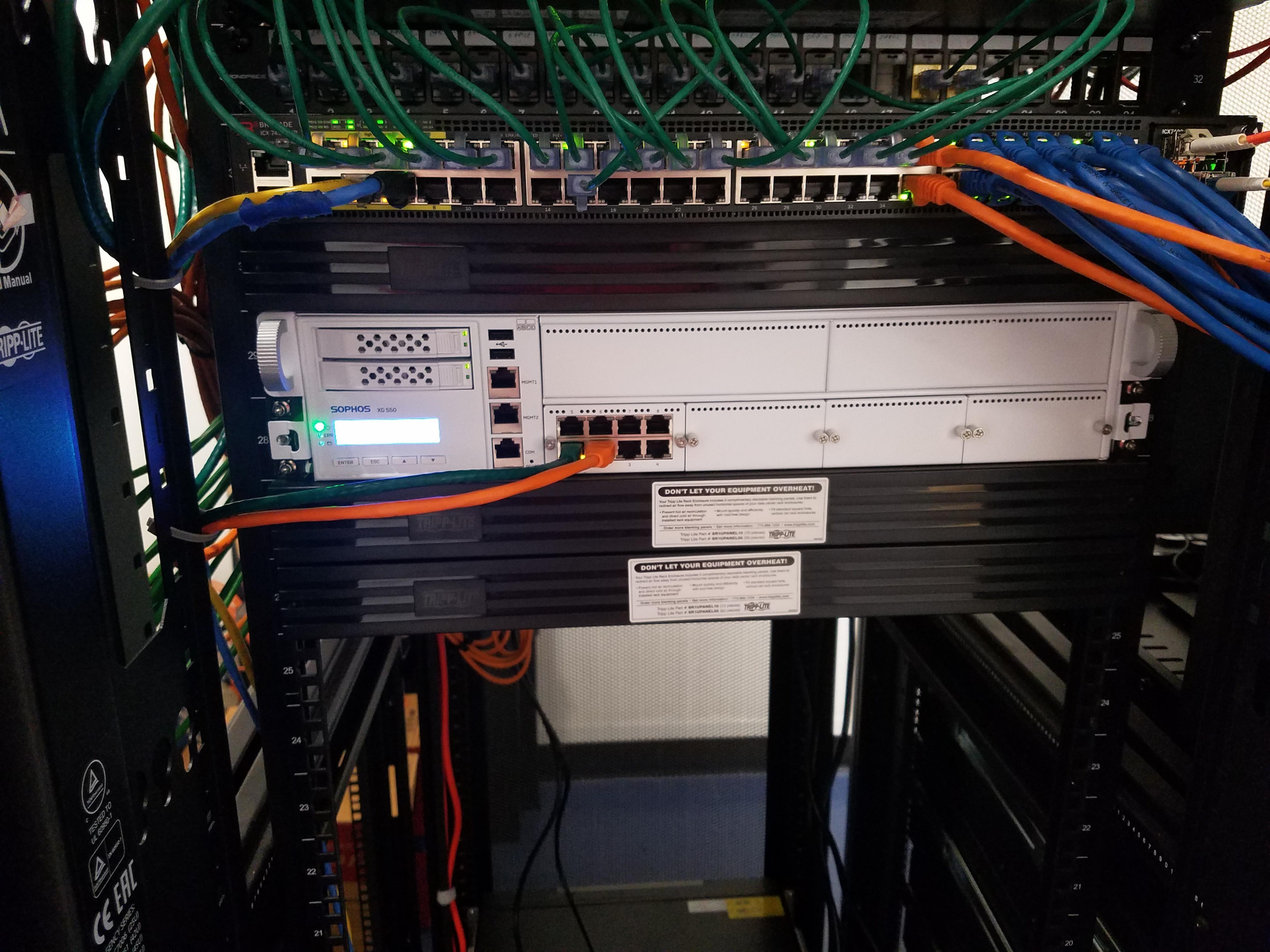
 Network security is becoming more necessary as attacks become more sophisticated and diverse. Accessing the network of an organization is a gold mine for hackers. Once a network is breached, there many different types of cyber attacks that the cyber criminals can employ to disrupt your organization's operations. Encryption of precious files, stealing of personal information, and impersonating executives in a phishing attack, are just a few of the tactics that these criminals employ. So what can you do when it comes to network security? You have to protect all entry points from these attacks. Specifically, we recommend considering the following five network security threats when preparing against such attacks.
Network security is becoming more necessary as attacks become more sophisticated and diverse. Accessing the network of an organization is a gold mine for hackers. Once a network is breached, there many different types of cyber attacks that the cyber criminals can employ to disrupt your organization's operations. Encryption of precious files, stealing of personal information, and impersonating executives in a phishing attack, are just a few of the tactics that these criminals employ. So what can you do when it comes to network security? You have to protect all entry points from these attacks. Specifically, we recommend considering the following five network security threats when preparing against such attacks.
1. Wired Network Threats
When comparing wireless vs wired network threats, wireless get the bulk of the attention due to its lack of "physical fences" but wired network threats cannot be ignored. Wired networks threats result from hackers having physical access to a network jack or cable. You can protect yourself from wired network attacks by auditing and mapping your network to ensure that you have an inventory of all access points and endpoints that have direct access to the network. Developing an inventory and physically securing the network are two simple steps that you can take to secure your network today. For more tips on securing your wired network, see 8 ways to improve wired network security.
2. Wireless Network Threats
It is easier for a cyber attacker to access unprotected wireless networks compared to wired networks. Wireless networks use radio waves to carry data between the network and end users and it can be very difficult to protect those radio waves from being intercepted. Cyber criminals can eavesdrop on wireless networks as long as they are in range of the signal. To protect against wireless network threats, organizations should encrypt their data, enable web filtering and implement comprehensive endpoint protection to protect against malicious software.
3. BYOD Security Risks
As illustrated in our previous post, Why Mobile Device Protection is Important | BYOD Security Risks, 72% of organizations permit the use of personal devices for work purposes. This statistics may seem normal for most organizations, but it can make for an security disaster if not prepared. The use of mobile devices adds another concern for IT managers.
- 24% of adults keep track of their personal and work passwords on one of their devices (PEW Research Center).
- 15% of large organizations had a data breach involving mobile devices in 2015 (HM Gov’t, Information Security Breaches Survey 2015).
- Data breaches involving mobile devices doubled every year (HM Gov’t, Information Security Breaches Survey 2015).
- 40% of companies reported missing devices in Q4 of 2015 (Security Magazine).
- 8% of companies enforce OS updates (Security Magazine).
Organizations need to have and enforce a formal BYOD policy. They also need to accept that the trend of increased use of personal devices will continue. Organizations cannot afford to ignore this trend and have to prepare for it by investment in the proper mobile protection. To view Pine Cove Consulting's solution, watch our webinar on the topic here:
4. Firewall Protection
Wanna, Petya, and other ransomware attacks have crippled countless organizations. Together, these two attacks have infected hundreds of thousands of computers all around the globe. These particular attacks spread by exploiting a vulnerability in Microsoft’s Server Message Block (SMB) network file-sharing protocol. This protocol is ubiquitous on corporate LANs and allows computers to discover each other for the purpose of sharing files and other resources like printers. It can also be used for file sharing outside the firewall if the necessary ports (TCP 139 and/or 445) are opened or forwarded on the firewall. Using the right firewall can prevent against these types of cyber attacks. Firewalls that are able to communicate with other aspects of your security are going to have the best chance at protecting against network security threats. Pine Cove recently introduced the Sophos XG V17 Firewall in the following webinar:
5. Employee error
Let's say you've protected against all of the above network security threats. Does this mean you are safe? The truth is that there is no perfect security system but the best security system has to account for employee error. In fact, according to Cision, over 90% of all types of cyber attacks are successfully executed with information stolen from employees who give away their accesscredentials to hackers. A combination of educational trainings and preventative technology is the best way to combat employee error.
Conclusion
Securing your network needs to be one of the main technological priorities for any organization. With so many different network security threats, how can you prepare? First you need to assess your current technology to identify holes in your network. Then you need to create a strategic plan to address the holes to ensure that your assets are protected. With so many different types of attacks and even more resources to protect you, this can get confusing. We offer a free IT assessment to help you get started. Sign up by clicking the button below.