What is ransomware?
Ransomware is a type of malware; malware is a catch-all term designed to disrupt and stop a device, application, or software from running correctly. Ransomware attacks a user's device and locks files, applications, or the device until the user pays a set amount of money. In many attacks, the hacker leaks data from files and gains access to sensitive information, ultimately compromising the organization's data security. According to Cybersecurity Company and PCC partner Sophos, the average ransom paid per organization was $170K in 2020. Ransomware attacks are not just costly but increasingly sophisticated. Cybercriminals use a blend of human-led and automated approaches, which overstretch IT teams...so how does an attack start?
Attacks commonly start in 3 ways:
- Via phishing emails containing malicious attachments/links
- Via Remote Desktop Protocol (RDP) and other remote access holes
- Via under drive-by downloading, people visiting infected websites
What does an attack look like?
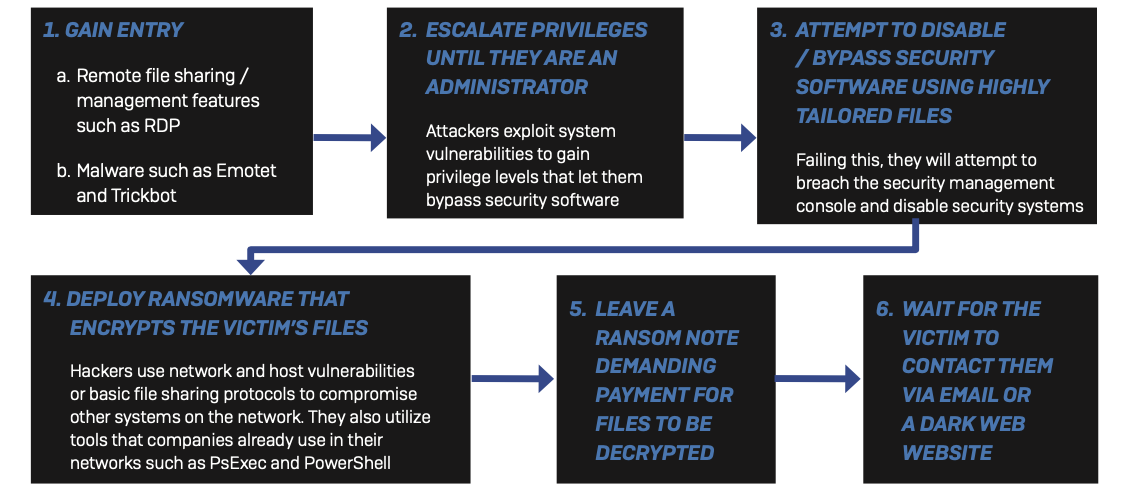
Image from Sophos, Pine Cove's Cyber Security Partner
Best Practices to Avoid Ransomware Attacks
- Patch early, patch often.
- Back up regularly and keep a recent backup copy off-line and off-site
- Implement a disaster recovery plan that covers the restoration of data
- Enable file extensions to help identify uncommon file types you usually wouldn't receive
- Open JavaScript (.JS) files in Notepad to block any malicious code
- Don't enable macros in document attachments received via email.
- Be cautious about unsolicited attachments.
- Monitor administrator rights to make sure new users, potential cybercriminals, were not added without your permission
- Stay up to date with security features in your business applications.
- Regulate external network access
- Use strong passwords and avoid reusing passwords.
- Keep an eye on your supply chain; only work with trusted companies.
- Understand the ins and outs of your cybersecurity platform
- Invest in high-quality IT support services if your IT team is overloaded
- Firewall. Firewall. Firewall. Firewalls come in all shapes and sizes that can protect your IT infrastructure, like emails, servers, devices, etc.
What Pine Cove Recommends
Pine Cove Consulting recommends having a complete cybersecurity bundle; firewall, server security, endpoint protection, email, and mobile security. However, it's not easy to know how well your coverage stands up against current ransomware sophistication. If you want to learn about the gaps in your cybersecurity infrastructure, click here or the button below. Pine Cove will reach out to complete the Gap Analysis Report for your organization. The report's purpose is to provide you with an overview of your cybersecurity posture based on cyber-threat trends and the protection available to combat those threats. Our goal is to provide you with the education and information needed to secure your organization to the best of your ability.



.png)








