 When people think cyber-security, they think endpoints, networks, servers, firewalls, etc. Mobile devices hardly make the top of the list, but maybe they should. With the rise of the BYOD (bring your own device) organization culture, organizations are being flooded with new devices into their network constantly. Companies are now encouraging employees to use their personal devices for work purposes. In fact, according to Forbes, 39% of business have a formal BYOD policy. Even if they don't have a formal policy, 72% of organizations permit the use of personal devices for work purposes. This number will continue to grow. Cell phones and tablets of all shapes, sizes, and brands are used within organizations with no thought about the BYOD security risks. With the BYOD market size set to increase from $94 billion in 2014 to past $350 billion by 2022 (GMInsights), the time is now to start evaluating the BYOD security risks and implement a mobile device security plan.
When people think cyber-security, they think endpoints, networks, servers, firewalls, etc. Mobile devices hardly make the top of the list, but maybe they should. With the rise of the BYOD (bring your own device) organization culture, organizations are being flooded with new devices into their network constantly. Companies are now encouraging employees to use their personal devices for work purposes. In fact, according to Forbes, 39% of business have a formal BYOD policy. Even if they don't have a formal policy, 72% of organizations permit the use of personal devices for work purposes. This number will continue to grow. Cell phones and tablets of all shapes, sizes, and brands are used within organizations with no thought about the BYOD security risks. With the BYOD market size set to increase from $94 billion in 2014 to past $350 billion by 2022 (GMInsights), the time is now to start evaluating the BYOD security risks and implement a mobile device security plan.
BYOD Security Risks
The growth of BYOD brings many security risks. Here are some numbers to consider:
- 24% of adults keep track of their personal and work passwords on one of their devices (PEW Research Center).
- 15% of large organizations had a data breach involving mobile devices in 2015 (HM Gov’t, Information Security Breaches Survey 2015).
- Data breaches involving mobile devices doubled every year (HM Gov’t, Information Security Breaches Survey 2015).
- 40% of companies reported missing devices in Q4 of 2015 (Security Magazine).
- 8% of companies enforce OS updates (Security Magazine).
On top of the growth of BYOD, mobile device hacking is also on the rise. It is becoming more easy for hackers to access an organization's data through unprotected devices in the network.
How to Protect your Mobile Device
To fully protect your data, your organization needs a comprehensive solution. Pine Cove Consulting provides organizations with a variety of choices when it comes to a mobile device protection plan. Specifically, there are three options, Sophos Mobile Advanced, Sophos Mobile Standard, and Sophos Mobile Security for Andriod. See the table below for more information.

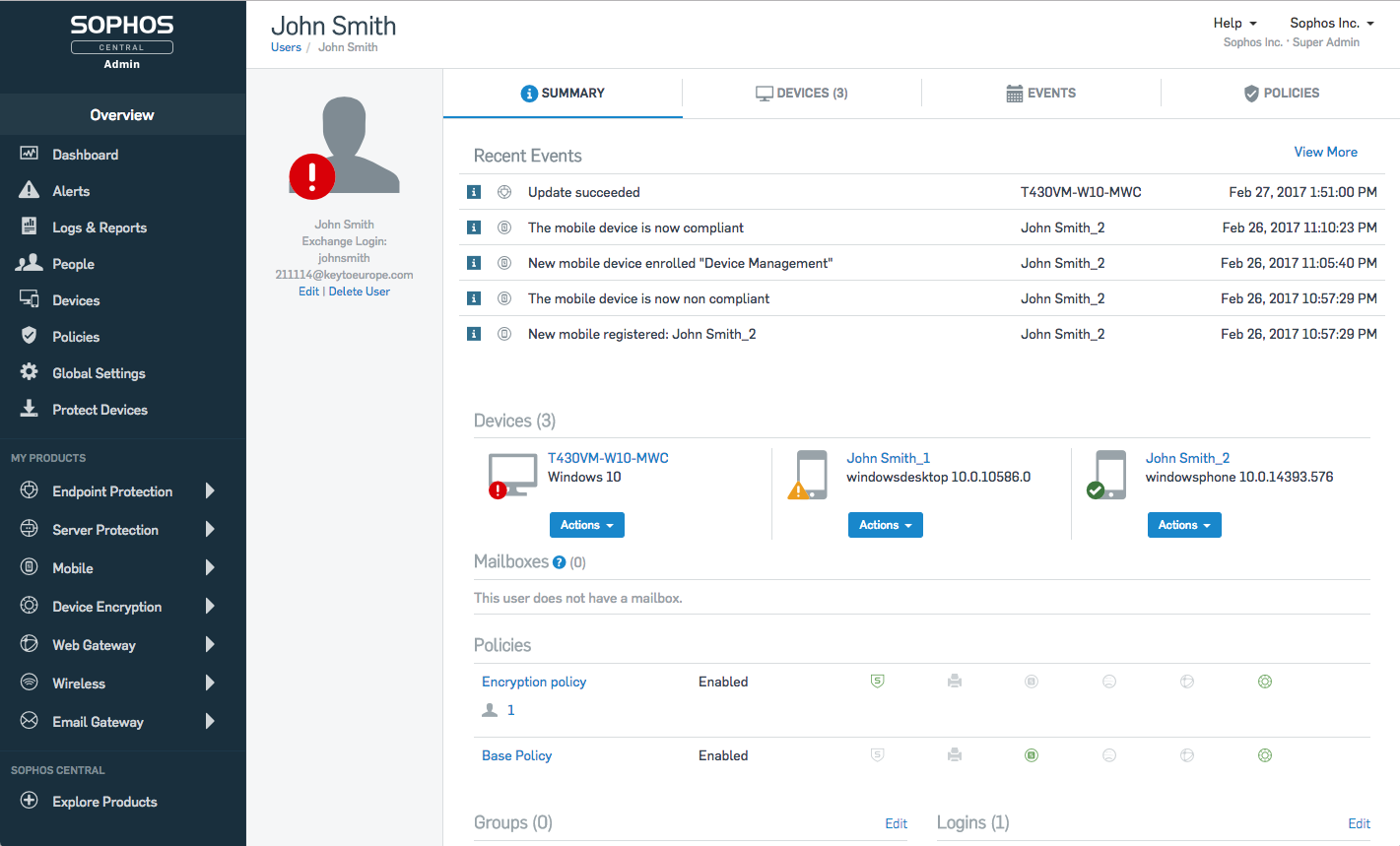
For those of you that are using Sophos already for some aspect of protection, Sophos mobile seamlessly integrates into your Sophos Central Platform. This makes for easy tracking and protection of mobile devices. To see the Sophos Central Platform and how Sophos Mobile is integrated into it, watch this quick video:
Conclusion
The growth of BYOD certainly isn't a bad thing. It allows employees more flexibility in their jobs. I am currently writing this post on my own personal computer and using my phone next to me to check my work emails. The benefits far outweigh the costs. Don't let the damage of a cyber attack prevent you from embracing the BYOD trend. Secure your devices with mobile device protection and have peace of mind with your pro BYOD policy. Contact us for a cyber risk assessment or for more information.
Read some more of our cyber-security blogs:
3 Major Types of Cyber Attacks
Why Sophos Security | Pine Cove Consulting's Top 5 Reasons
3 Phishing Attack Examples